3d.1 # BORDER GATEWAY PROTOCOL STATE AND EXPLAIN
BGP is a standard exterior gateway protocol (EGP) as opposed to RIP, OSPF and EIGRP which are interior gateway protocols (IGP). BGPv4 is the current standard deployment. BGP is considered a ‘Path Vector’ routing protocol. BGP was not built to route within an Autonomous System (AS) but rather to route between AS’s. BGP maintains a separate routing table based on shortest AS Path and various other attributes as opposed to IGP metrics like distance or cost. BGP is the routing protocol of choice on the Internet. Essentially, the internet is a collection of interconnected Autonomous Systems. BGP Autonomous Systems are assigned an Autonomous System Number (ASN), which is a 16-bit number range from 1-65535. A specific subnet of this range 64512-65535 has been reserved for private (or internal) use. And BGP utilizes TCP for reliable transfer of its packets on port 179.
# Types of customer in BGP# Types of Autonomous System Number
1) 2 byte AS --> 16 bit = (0 - 65535)
2) 4 byte AS --> 16 bit.16 bit = (0 - 65535).(0 - 65535)
As per simple language there are two types of BGP Autonomous system numbers: Private and Public. The Public AS numbers range from 1 to 64511 and the Private AS numbers range from 64512 to 65535. The Private AS numbers are used to divide large AS into many small AS numbers for the sole purpose of conserving Public AS numbers.
BGP is also completely unncecessary if there is only one connection to an external AS (Such as the Internet). There are over 10,000 routes on the Internet and interior route should not be needlessly burdened.
BGP should be used under the following circumstances:There are two types of BGP neighbor relationships:
iBGP Peers – BGP neighbors within the same autonomous system.
eBGP Peers – BGP neighbors connecting separate autonomous systems.
# BGP Peers Message
# BGP Peers State
As a BGP peer session is forming, it will pass through several states. This process is known as the BGP-FSM.
3d.2 # Lab and Verify of BGP Route Peering with AS
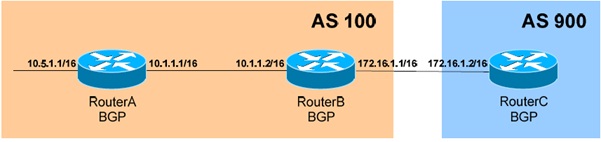
1. BGP Neighbors Diagram : -
Configuration: The first step in configuring of BGP is to enable, the BGP process and specify the Router’s Autonomous System: -
RouterB (config)# router bgp 100
RouterB is now a member of AS 100. Next, neighbor relationships must be established. To configure a neighbor relationship with a router in the same Autonomous System (iBGP Peer):
RouterB (config)# router bgp 100
RouterB (config-router)# neighbor 10.1.1.1 remote-as 100
To configure a neighbor relationship with a router in a separate Autonomous System (iBGP Peer):
RouterB (config)# router bgp 100
RouterB (config-router)# neighbor 172.16.1.2 remote-as 900
Notice that the syntax is the same and that the remote-as argument is always used, regardless if the peering is iBGP or eBGP.
For stability purpose, the source interface used to generate updates to a particular neighbor can be specified:
RouterB (config)# router bgp 100
RouterB (config-router)# neighbor 172.16.1.2 update-source lo0
RouterC must then point to RouterB’s loopback (assume the address is 1.1.1.1/24) in its neighbor statement:
RouterB (config)# router bgp 100
RouterB (config-router)# neighbor 1.1.1.1 remote-as 100
Notice, RouterC must have a route to RouterB’s loopback in its routing table.
To authenticate updates between two BGP peers:
RouterB (config)# router bgp 100
RouterB (config-router)# neighbor 172.16.1.2 password @#$@123
To globally adjust the keepalive and Hold-timers for all neighbors:
RouterB (config)# router bgp 100
RouterB (config-router)# timers bgp 30 90
To adjust the timers for a specific neighbor (Which overrides the global timer configuration):
RouterB (config)# router bgp 100
RouterB (config-router)# neighbor 172.16.1.2 timer 30 90
To view the status of all bgp neighbors:
RouterB # show ip bgp neighbors
RouterB # show ip bgp neighbors 172.16.1.2
To disable BGP synchronization:
RouterB (config)# router bgp 100
RouterB (config-router)# no syunchroniztion
2. Originating Prefixes of BGP : There are three ways to originate a prefix (in other works, advertise a network) into BGP.
• By using network statements.
• By using aggregate-address statements.
• By redistributing an IGP into BGP
Origin Diagram : -
Consider the above example. RouterB may inject the 10.5.0.0/16 network into BGP using the network command. However, unless that route is in the local routing table (in this case, via an IGP), RouterB will not advertise the route to RouterC.
Configuration:RouterB (config)# router bgp 100
RouterB (config-router)# neighbor 172.16.1.2 remote-as 900
RouterB (config-router)# network 10.5.0.0 mask 255.255.0.0
3. BGP Route-Reflectors :Recall that BGP requires all iBGP peers to be fully meshed.Route-Reflectors allow us to bypass this restriction. Fewer neighbor connections will result in less bandwidth and CPU usage. BGP updates will flow from the server to the clients without the client having to interact with each other.
Reflectors Diagram : -
Consider the above example. In AS 100, there are three BGP speakers. Normally, these iBGP peers must be fully-meshed. For example, RouterB would need a neighbor statement for both RouterA and RouterD. As an alternative, RouterA can be configured as a route-reflector server. Both RouterB and RouterD would only need to peer with RouterA. All route-reflector specific configurations take place on the route reflector server:
Configuration:RouterA (config)# router bgp 100
RouterA (config-router)# neighbor 10.2.1.2 remote-as 100
RouterA (config-router)# neighbor 10.2.1.2 route-reflector-client
RouterA (config-router)# neighbor 10.1.1.2 remote-as 100
RouterA (config-router)# neighbor 10.1.1.2 route-reflector-client
4. BGP Confederations : Confederations are an alternative method to alleviate the requirement that all iBGP routers be fully meshed. Confederations are essentially AS’s within an AS, and are sometimes referred to as sub-AS’s. In the above example, RouterA belongs to AS 777 and RouterB belongs to AS 888. Both of those AS’s belong to a parent AS of 300. RouterA and RouterB will form an eBGP peer session.
Confederations Diagram : -
RouterB (config)# router bgp 888
RouterB (config-rotuer)# bgp confederation identifier 300
RouterB (config-rotuer)# bgp confederation peer 777
RouterB (config-rotuer)# neighbor 10.1.1.1 remote-as 777
RouterB (config-rotuer)# neighbor 172.16.1.2 remote-as 500
RouterC will be unaware of RouterB’s confederation status. Thus, RouterC’s neighbor statement will point to ASS 300 and not AS 8888
RouterC (config)# router bgp 500
RouterC (config-router)# neighbor 172.16.1.1 remote-as 300
5. BGP Attributes : There are two types of attributes, further two categories of each.
a) Well-Known – Mandatory – Discretionary
b) Optional – Transitive – Non Transitive
| Well-Known mandatory | Well-Known discretionary | Optional transitive | Optional non transitive |
|---|---|---|---|
| Origin | Local preference | Community | Multi-Exit-Discriminator |
| AS-Path & Next-Hop | Auto Aggregate | Cluster List | Aggregator |
6. BGP Routing Decision : BGP makes routing decisions based on paths, defined by rules or network policies set by network administrators. BGP routers typically receive multiple paths to the same destination. The BGP best path algorithm decides which is the best path to install in the IP routing table and to use for traffic forwarding..
Routing Decision Diagram : -
RouterA(config)# router bgp 100
RouterA(config)# neighbor 10.1.1.2 weight 200
• Prefer local preference (Within AS)
RouterA(config)# router bgp 100
RouterA(config)# bgp default local-preference 200
RouterB(config)# router bgp 100
RouterB(config)# bgp default local-preference 300
• Prefer AS-Path Prepend (Applied to outbound routes)
RouterB(config)# access-list 5 permit 10.5.0.0 0.0.255.255
RouterB(config)# route-map ASPREPEND permit 10
RouterB(config-route-map)# match ip address 5
RouterB(config-route-map)# set as-path prepend 200 200
RouterB(config-route-map)# route-map ASPREPEND permit 20
RouterB(cofig-route-map)# exit
RouterB(config)# router bgp 100
RouterB(config-router)# neighbor 172.16.1.2 route-map ASPREPEND out
• Prefer AS-Path Filtering (Routes can be filtered based on AS-Path values)
RouterF(config)# ip as-path access-list 15 permit _100$
RouterF(config)# route-map ASFILTER permit 10
RouterF(config-route-map)# match as-path 15
RouterF(cofig-rout-map)# exit
RouterF(config)# router bgp 50
RouterF(config-router)# neighbor 10.5.1.1 route-map ASFILTER in
• Prefer Origin (Define the originating source of the route i IGP > e EGP > ? Incomplete)
RouterB# show ip bgp
Network Next Hop Metric LocPrf Weight Path
*> 10.5.0.0 10.1.1.1 0 0 0 i
*> 192.168.1.0 172.16.1.2 0 100 0 900 ?
• Prefer MED (Dictating the best input path into the AS)
RouterB(config)# access-list 5 permit 10.5.0.0 0.0.255.255
RouterB(config)# route-map SETMED permit 10
RouterB(config-route-map)# match ip address 5
RouterB(config-route-map)# set metric 200
RouterB(cofig-route-map)# exit
RouterB(config)# router bgp 100
RouterB(config-router)# neighbor 172.16.1.2 route-map SETMED out
RouterE(config)# router bgp 100
RouterE(config-router)# bgp deterministic-med
Router(cofig-route)# exit
RouterE(config)# router bgp 100
RouterE(config-router)# bgp always-compare-med
RouterE(cofig-route)# exit
RouterB(config)# access-list 5 permit 10.5.0.0 0.0.255.255
RouterB(config)# route-map MED_INTERNAL permit 10
RouterB(config-route-map)# match ip address 5
RouterB(config-route-map)# set metric-type internal
RouterB(cofig-route-map)# exit
RouterB(config)# router bgp 100
RouterB(config-router)# neighbor 172.17.1.2 route-map MED_INTERNAL out
• Prefer Community (Router can make policy based on router’s communities membership)
RouterA(config)# ip bgp-community new-format
RouterB(config)# access-list 5 permit 10.5.0.0 0.0.255.255
RouterB(config)# route-map COMMUNITY permit 10
RouterB(config-route-map)# match ip address 5
RouterB(config-route-map)# set community no-export
RouterB(config)# route-map COMMUNITY permit 20
RouterB(config)# router bgp 100
RouterB(config-router)# neighbor 172.16.1.2 send-community
RouterB(config-router)# neighbor 172.16.1.2 route-map COMMUNITY out
RouterB(config-router)# exit
RouterB(config)# route-map COMMUNITY permit 10
RouterB(config-route-map)# match ip address 5
RouterB(config-route-map)# set community no-export additive
RouterB(config)# route-map COMMUNITY permit 20
7. eBGP TTL Security : The BGP support for TTL Security Check is a mechanism to protect eBGP peering sessions from attacks that can be caused using forged IP packets. This feature can prevent from hosts who attempts to hijack an eBGP session. This feature is used to protect only eBGP peering sessions, and is not supported for iBGP peers.
TTL Security Diagram : -
RouterA (config)# router bgp 100
RouterA (config-rotuer)# neighbor 172.17.1.2 remote-as 900
RouterA (config-rotuer)# neighbor 172.16.1.2 ttl-security hops 4
RouterA (config-rotuer)# exit
RouterE (config)# router bgp 900
RouterE (config-rotuer)# neighbor 10.1.1.1 remote-as 100
RouterE (config-rotuer)# neighbor 10.1.1.1 ttl-security hops 4
RouterE (config-rotuer)# exit
Be updated into yourself and improve lives through DIT